This comprehensive guide aims to explore every facet of WhatsApp’s data security, focusing particularly on its end-to-end encryption. We will delve into the technical workings of E2EE, the measures WhatsApp takes to ensure data privacy, and how users can further protect their information. From addressing common myths and misconceptions to providing practical tips for enhancing security, this article serves as a one-stop resource for understanding WhatsApp’s commitment to data security.
Whether you are an individual user concerned about your personal privacy or a business looking to safeguard your professional communications, this guide will provide valuable insights and actionable advice. Let's embark on this journey to understand how WhatsApp keeps our conversations secure and what we can do to stay protected in the digital landscape.
What is WhatsApp Data Security?
With over 3 billion users worldwide, WhatsApp has become a crucial platform for both personal and professional communication. Because of its popularity, it's a prime target for security threats. That’s why WhatsApp emphasizes strong data security to protect user privacy.

At its core, WhatsApp’s data security ensures that your messages, calls, photos, videos, and other shared content are safe from unauthorized access. The app relies on features like end-to-end encryption and secure backups to keep your conversations private and protected from falling into the wrong hands.
What is End-to-End Encryption in WhatsApp?
In the realm of digital communication, the term "end-to-end encryption" (E2EE) has become a cornerstone of data security. But what exactly does it mean, and why is it so important?
End-to-end encryption is a method of secure communication that ensures that only the communicating users can read the messages. In simple terms, it means that your messages are encrypted on your device and only decrypted on the recipient’s device. Even if the messages pass through intermediate servers, including WhatsApp’s own servers, they remain encrypted and unreadable by anyone other than the intended recipient.
Looking for strategies to sell on WhatsApp?
Here are some of the kickass tips on how to sell on WhatsApp easily!
How Does WhatsApp Encryption Work?
Here's a simple explanation of how E2EE works in WhatsApp:
- Key Generation
- When you first install WhatsApp, the app generates a pair of cryptographic keys for your device: a public key and a private key. The public key is shared with other users, while the private key remains securely stored on your device.
- Key Exchange
- When you start a conversation, WhatsApp automatically exchanges public keys between your device and the recipient’s device. This happens silently in the background, ensuring a seamless user experience.
- Message Encryption
- When you send a message, WhatsApp encrypts it on your device using the recipient’s public key. This process transforms your message into ciphertext, an unreadable format that can only be decrypted by the recipient’s private key.
- Server Relay
- The encrypted message (ciphertext) is sent to WhatsApp’s servers, which act as relays to forward it to the recipient’s device without decrypting it.
- Message Decryption
- Upon receiving the ciphertext, the recipient’s device uses its private key to decrypt the message, converting it back into its original, readable format.
- Message Display
- The decrypted message is then displayed on the recipient’s device.
How to Enable End-to-End Encryption in WhatsApp?
You don’t have to manually enable end-to-end encryption on WhatsApp, it’s turned on by default for all personal chats and calls.
Every message, photo, video, and voice note you send is automatically encrypted.
However, to ensure your backups are encrypted, follow these steps:
Step 1: Open WhatsApp and go to Settings.
Step 2: Tap Chats > Chat Backup.
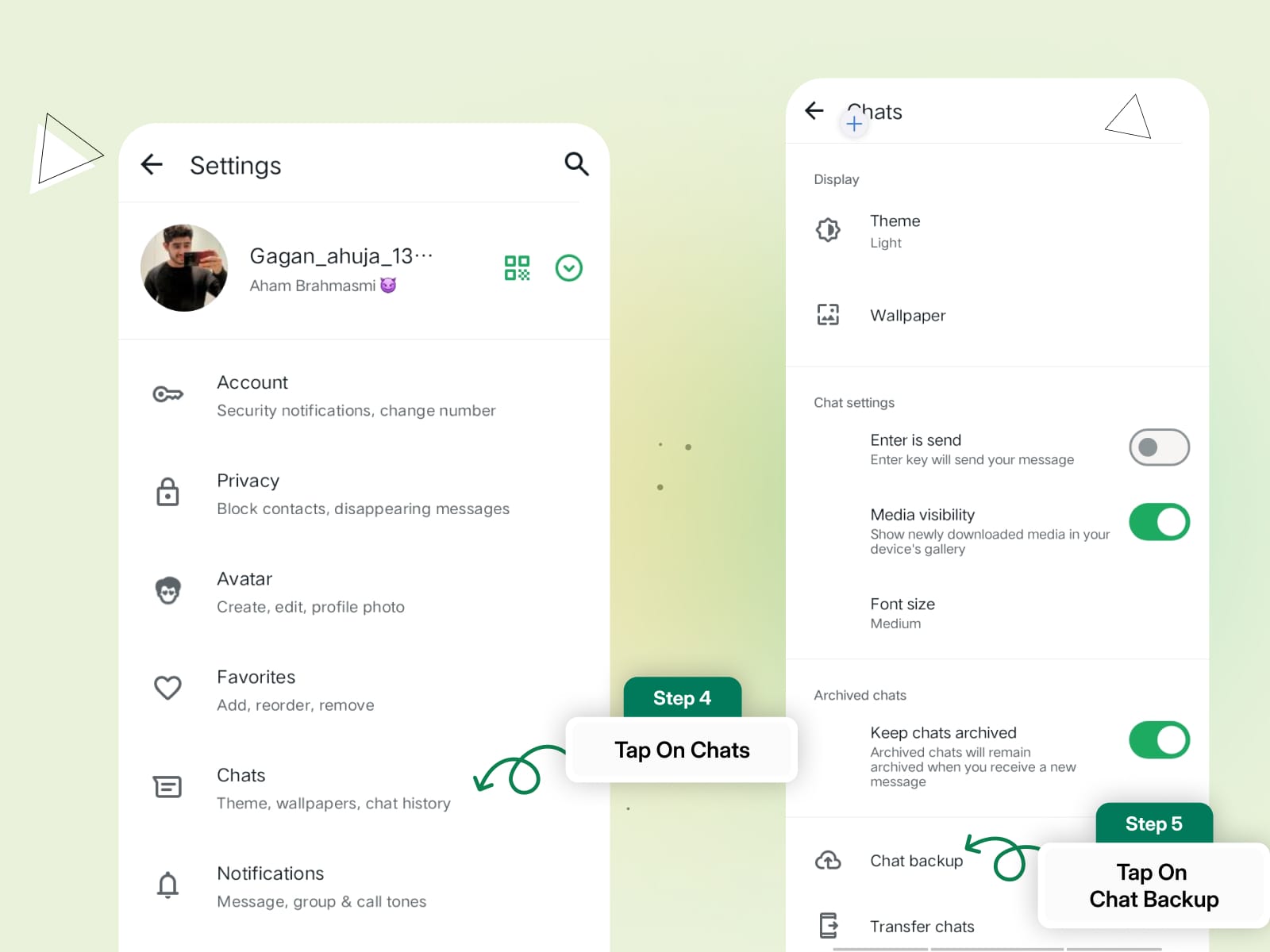
Step 3: Select End-to-End Encrypted Backup.
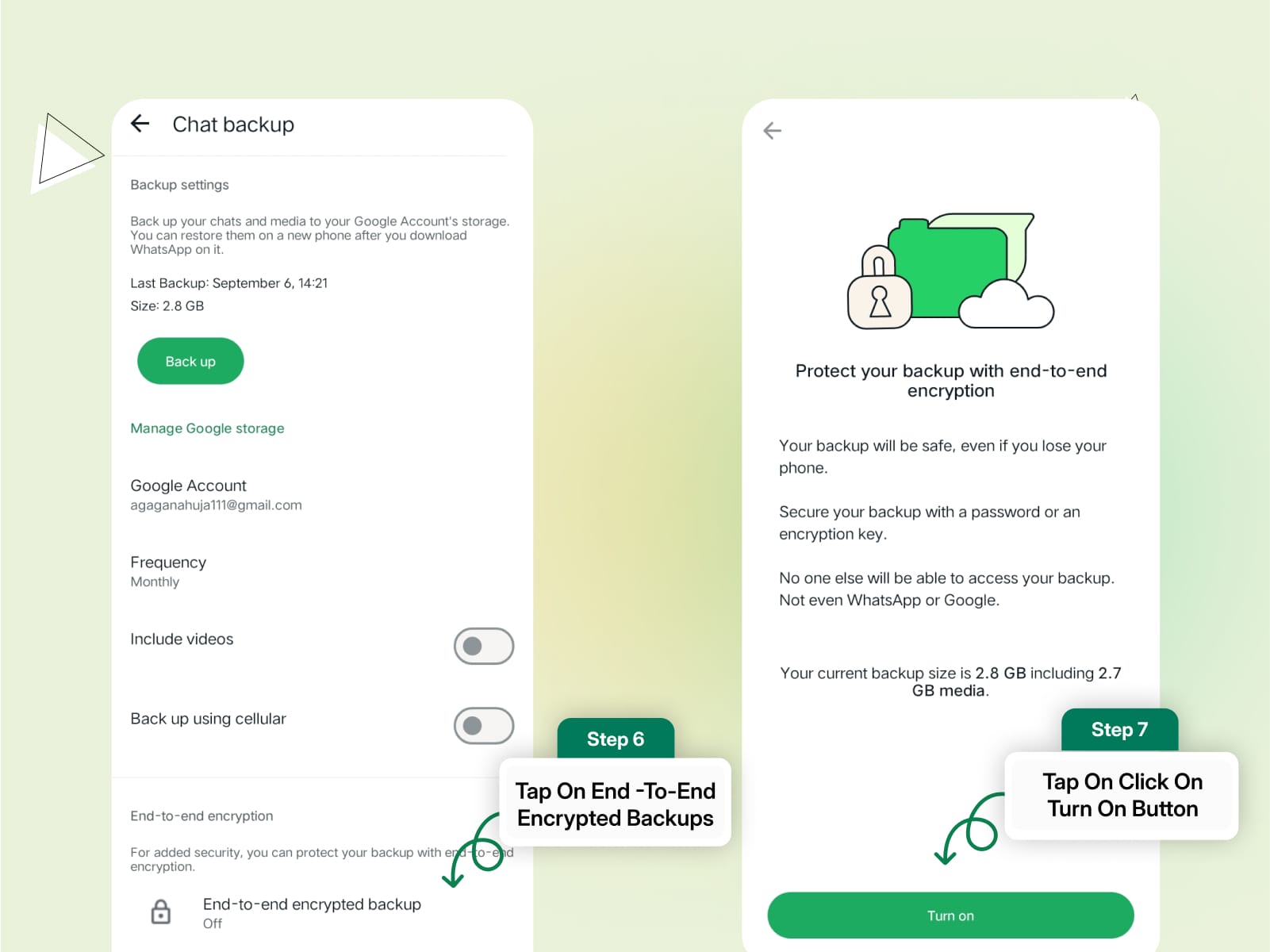
Step 4: Follow the prompts to create a password or use a 64-digit encryption key.
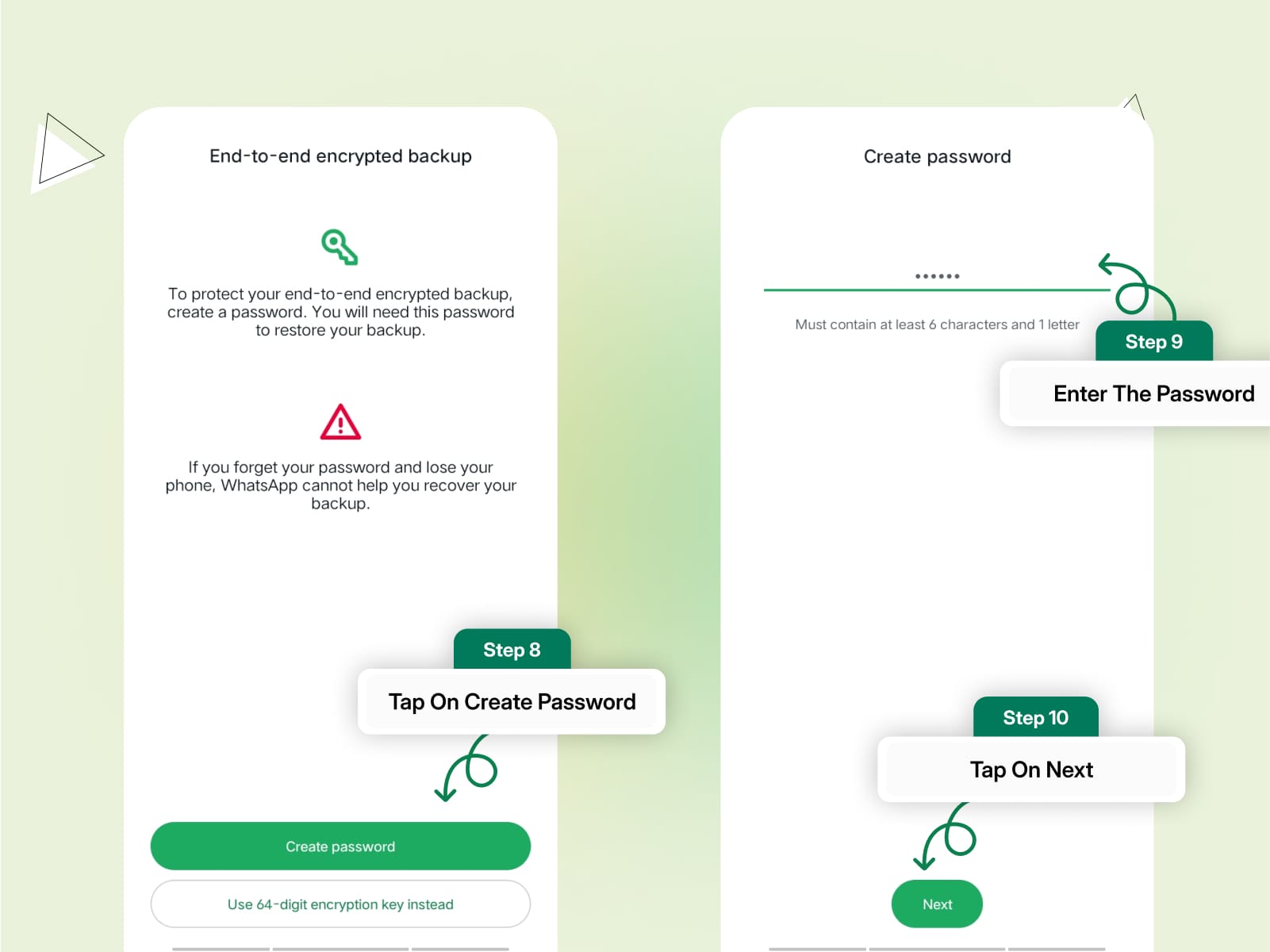
Step 5: Tap Create to enable encrypted backups.
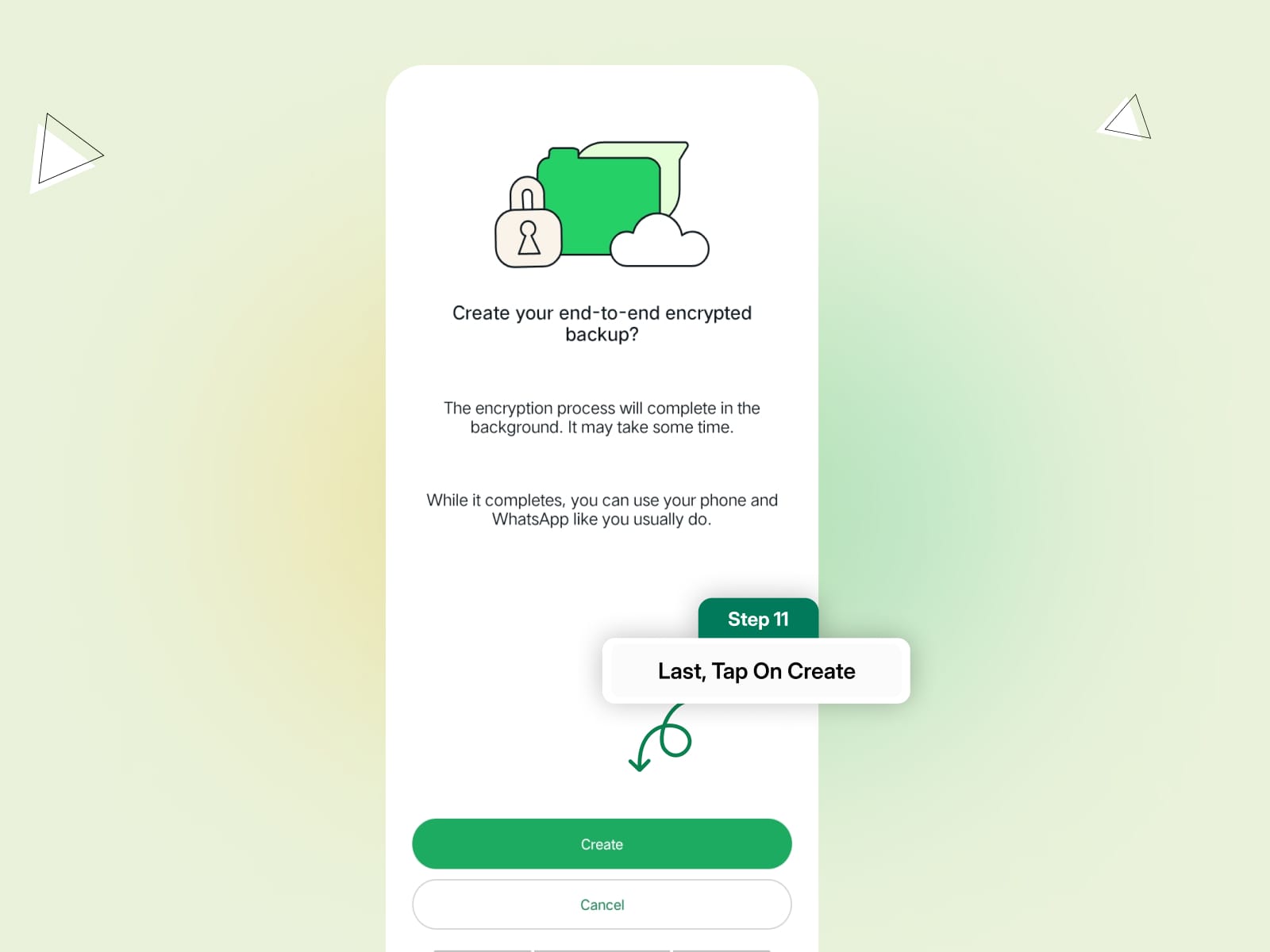
Now, even your WhatsApp backups are secured with end-to-end encryption.
How to Disable End-to-End Encryption in WhatsApp?
You can't disable end-to-end encryption for personal chats and calls as it’s a built-in feature, however, you can disable it for your chat backups.
Here’s how to turn off encryption for your backups:
Step 1: Open WhatsApp and go to Settings.
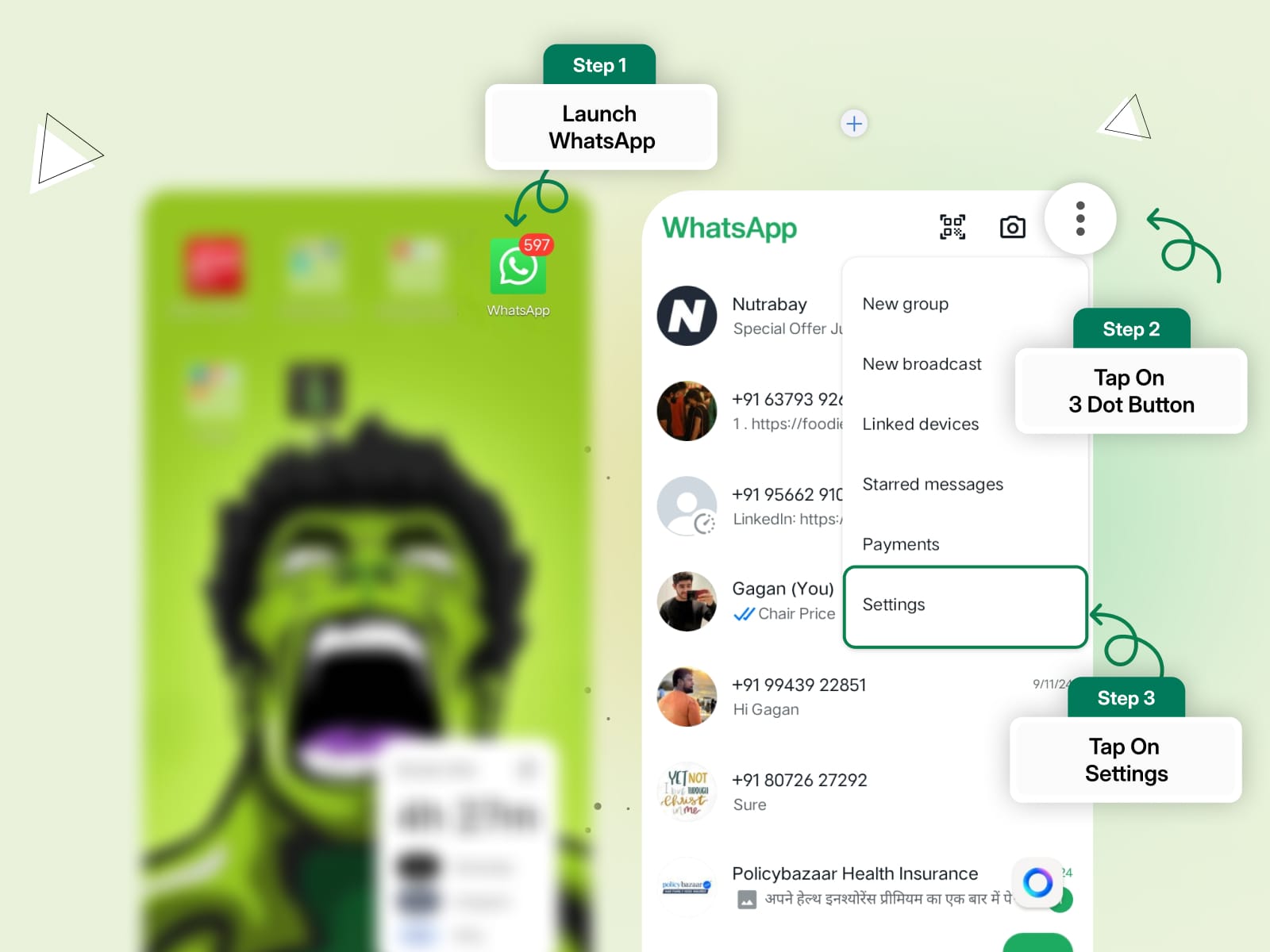
Step 2: Tap Chats > Chat Backup.
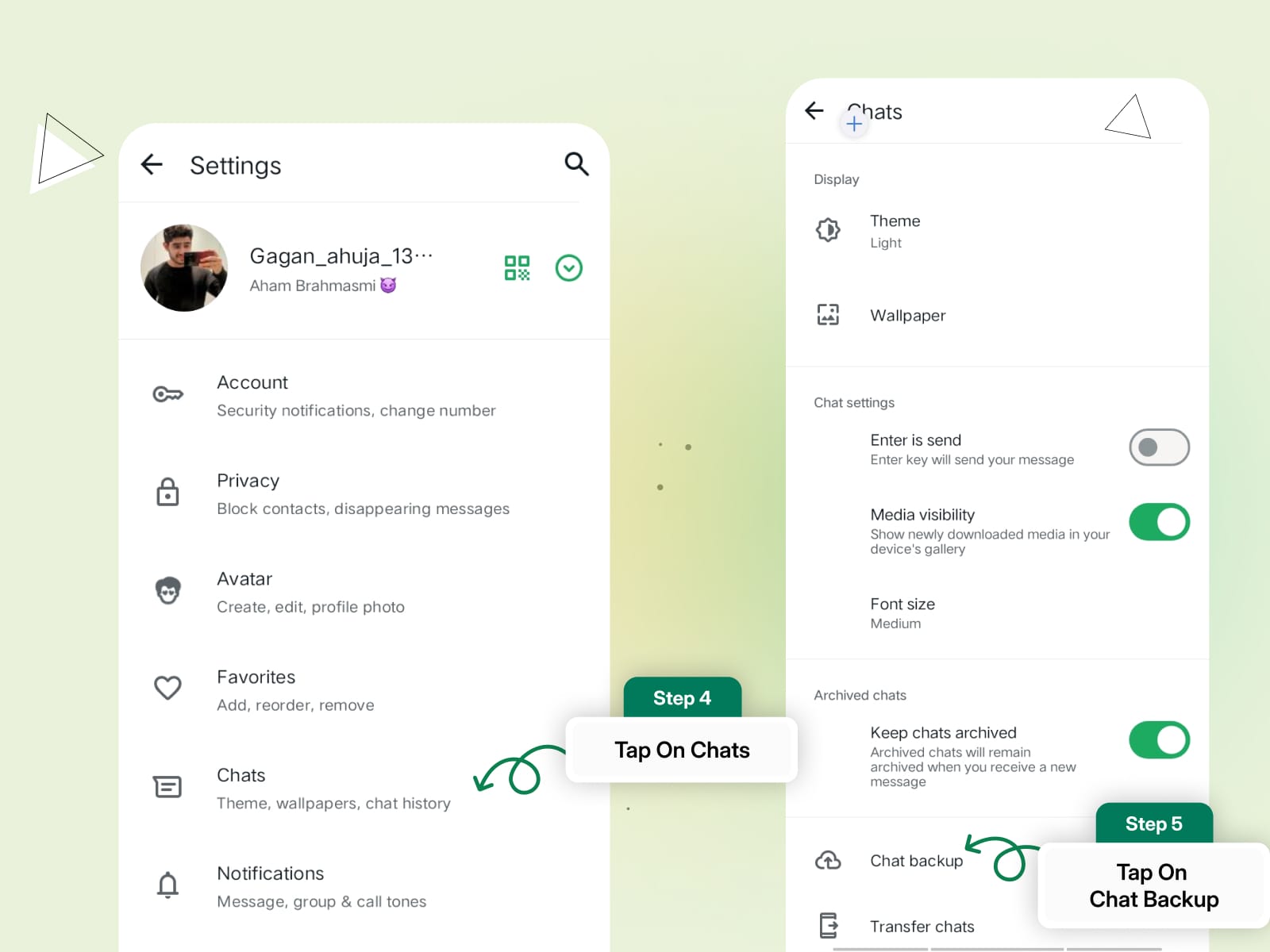
Step 3: Select End-to-End Encrypted Backup.
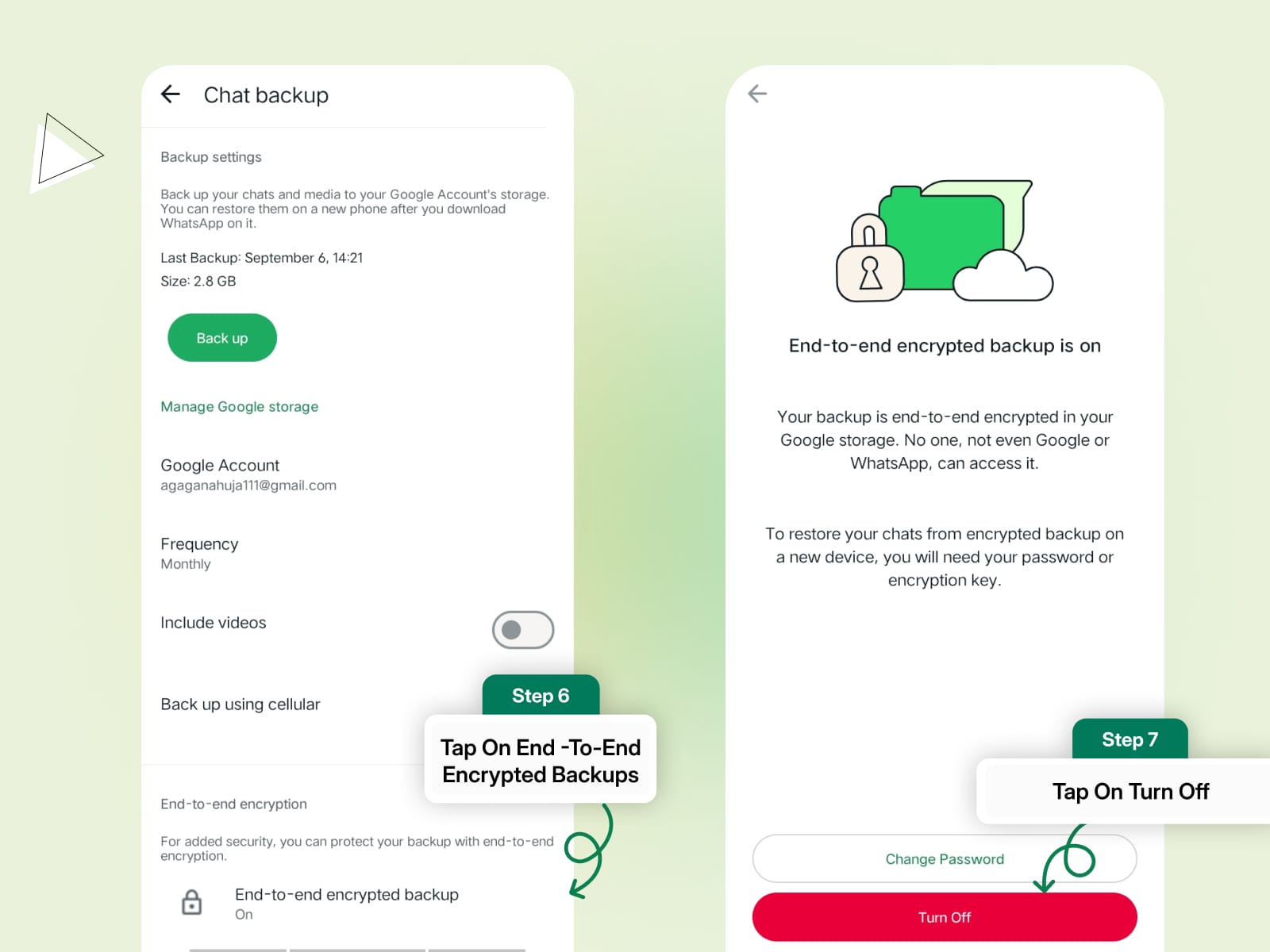
Step 4: Tap Turn Off.
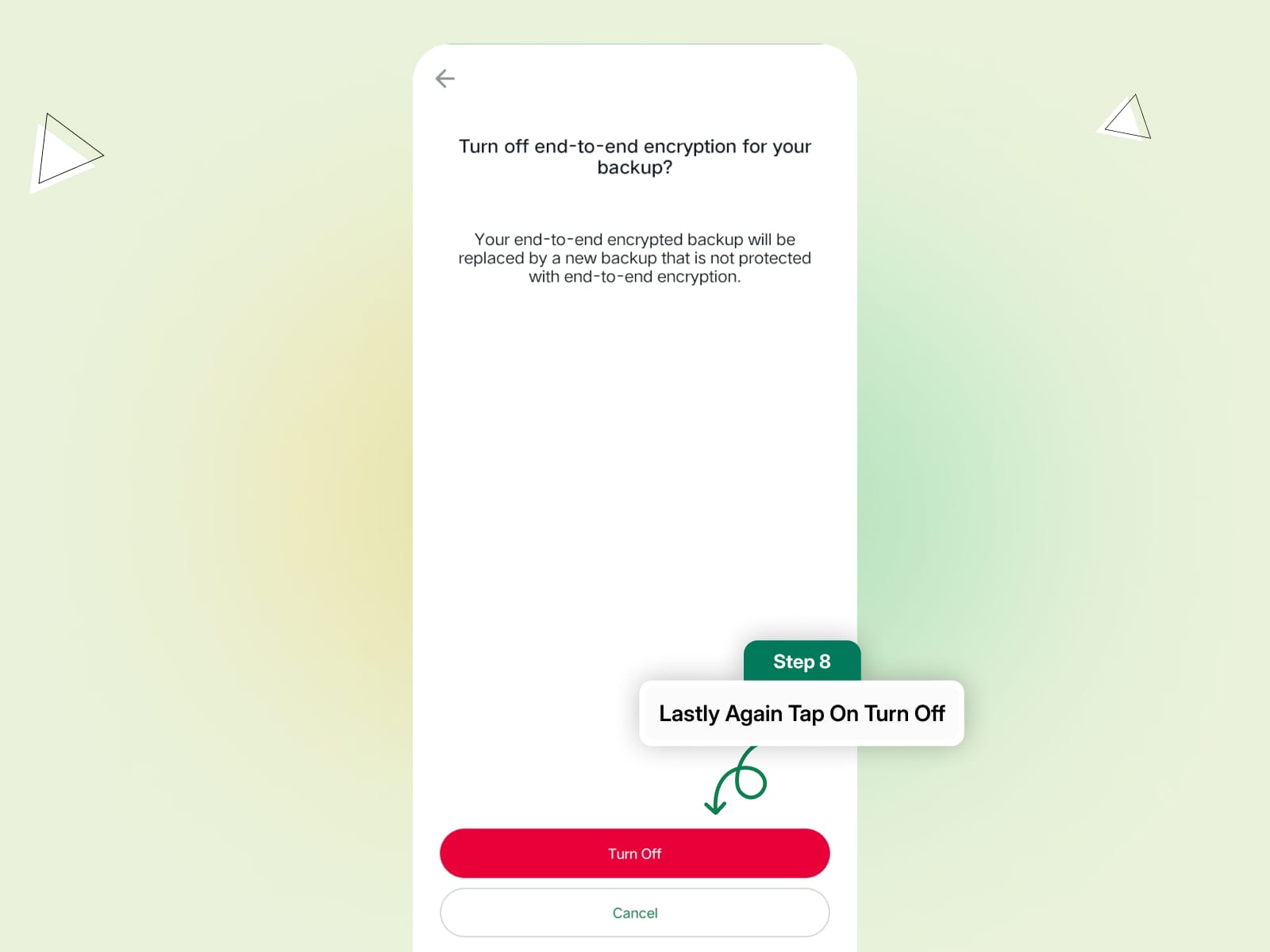
Enter your password or encryption key to confirm and disable encrypted backups.
Once disabled, your future backups won’t be end-to-end encrypted, but your personal chats and calls will remain encrypted.
Benefits of WhatsApp End-to-End Encryption
Here are a few of the benefits and importance of WhatsApp End-to-End Encryption:
Confidentiality
E2EE ensures that only the sender and recipient can read the messages, providing a high level of confidentiality. This is crucial for maintaining the privacy of personal and sensitive information.
Protection Against Surveillance
E2EE protects against unauthorized surveillance by governments, hackers, or any other third parties. It ensures that communication remains private and inaccessible to unauthorized entities.
Preventing Data Breaches
Even if a service provider’s servers are compromised, E2EE ensures that the encrypted data remains unreadable without the private keys held by the users. This significantly reduces the risk of data breaches.
Building Trust in Communication Services
Knowing that their communications are end-to-end encrypted instils trust in users. It reassures them that their personal messages, photos, videos, and sensitive documents are protected, fostering a sense of security and confidence in using digital communication platforms.
Ensuring Business and Professional Communication Security
For businesses, E2EE is essential for safeguarding confidential client information, proprietary data, and trade secrets. It ensures that sensitive business discussions and transactions remain private and secure.
Personal Safety
E2EE is vital for individuals facing personal safety risks when disclosing sensitive information, including whistleblowers, activists, journalists, and individuals in oppressive regimes. Encrypted communication provides a lifeline for sharing crucial information while safeguarding their identity.
Preserving User Autonomy
E2EE empowers users to control their data and who has access to it. It prevents service providers from monetizing user data without consent and helps users maintain digital autonomy.
Legal and Ethical Compliance
Many countries and industries have regulations requiring user data protection and privacy. Implementing E2EE helps organizations comply with these legal requirements and maintain their ethical responsibilities toward users.
Mitigating Insider Threats
E2EE can also guard against insider threats within organizations. Employees with access to systems and data cannot read encrypted messages without decryption keys.
Global Standard for Privacy
E2EE has become a global standard for ensuring digital privacy. It has raised the bar for security across various communication platforms, encouraging the adoption of more robust encryption practices.
In summary, end-to-end encryption is a critical technology for ensuring the privacy and security of digital communications. By understanding how it works and its benefits, users can appreciate the importance of E2EE in protecting their data and maintaining trust in communication platforms like WhatsApp.
Read in-depth about the benefits of WhatsApp Business API HERE
Key Features of WhatsApp End-to-End Encryption
Understanding the key features and technical aspects of WhatsApp’s encryption can help users appreciate the robust security measures that protect their data.
This section delves into the details of the Signal Protocol, the encryption and decryption process, the double ratchet algorithm, and how end-to-end encryption (E2EE) extends to group chats, multimedia sharing, and voice and video calls.
Detailed Explanation of the Signal Protocol Used by WhatsApp
WhatsApp’s end-to-end encryption is built on the Signal Protocol, developed by Open Whisper Systems. The Signal Protocol is widely regarded as the gold standard for encrypted messaging. It combines several cryptographic techniques to ensure that messages are secure and private.
- Public Key Cryptography: Each user has a pair of cryptographic keys: a public key and a private key. The public key is shared with others, while the private key is kept secret.
- Session Initialization: When two users communicate for the first time, a session is established using the X3DH (Extended Triple Diffie-Hellman) handshake. This handshake allows the users to agree on a shared secret without ever transmitting it over the network.
How Messages Are Encrypted and Decrypted
- Key Generation: When a user installs WhatsApp, the app generates a pair of cryptographic keys: a public key and a private key. The public key is shared with WhatsApp’s servers, while the private key remains on the user's device.
- Key Exchange: When a user initiates a chat, WhatsApp automatically exchanges public keys between the communicating devices. This exchange allows the sender to encrypt messages using the recipient’s public key.
- Message Encryption: Each message is encrypted on the sender's device using the recipient’s public key. This process converts the message into ciphertext, which is unreadable without the corresponding private key.
- Server Relay: The encrypted message (ciphertext) is sent to WhatsApp’s servers, which relay it to the recipient’s device. At no point can WhatsApp’s servers decrypt the message.
- Message Decryption: Upon receiving the encrypted message, the recipient’s device uses its private key to decrypt the message, converting it back into its original readable form.
Explanation of Double Ratchet Encryption and Its Benefits
The Signal Protocol employs the double ratchet algorithm to enhance security. The double ratchet algorithm ensures forward secrecy and post-compromise security by constantly updating encryption keys. Here's how it works:
Initialization
When a session is first established, initial keys are generated using the X3DH handshake. These keys are used to encrypt the initial set of messages.
Ratchet Steps
- Diffie-Hellman Ratchet: After each message, a new Diffie-Hellman key pair is generated. The shared secret from this key exchange is used to derive new encryption keys.
- Symmetric Ratchet: In addition to the Diffie-Hellman ratchet, a symmetric ratchet is used to generate a new encryption key for each message. This key is derived from the previous key, ensuring that each message has a unique key.
Forward Secrecy
By frequently updating encryption keys, the double ratchet algorithm ensures that even if a key is compromised, only a limited set of messages can be decrypted. Previous and future messages remain secure.
E2EE in Group Chats and Multimedia Sharing
WhatsApp extends end-to-end encryption to group chats and multimedia sharing, ensuring that all forms of communication are secure.
Group Chats
- Each group chat has a unique encryption key. When a user sends a message to a group, the message is encrypted using the group’s encryption key. Each group member can decrypt the message using their private key, ensuring that only intended recipients can read it.
- The Signal Protocol ensures that group messages are encrypted individually for each member, maintaining privacy and security.
Multimedia Sharing
- When users share photos, videos, or other media files, these files are encrypted before being uploaded to WhatsApp’s servers. The encrypted files are then shared with the recipients, who can decrypt and view them using their private keys.
- This process ensures that multimedia content remains secure and private during transmission and storage.
How E2EE Works for Voice and Video Calls
WhatsApp uses end-to-end encryption to secure voice and video calls, ensuring that conversations remain private and cannot be intercepted.
Call Initialization
When a user initiates a voice or video call, a session is established using the Signal Protocol. This session uses the same encryption principles as text messages, ensuring that the call is encrypted end-to-end.
Encryption and Decryption
- Audio and video data are encrypted on the sender's device using the recipient’s public key. The encrypted data is transmitted to WhatsApp’s servers, which relay it to the recipient’s device.
- Upon receiving the encrypted data, the recipient’s device decrypts it using its private key, allowing the audio or video to be played.
Secure Transmission
Throughout the call, encryption keys are periodically updated to ensure ongoing security. This process prevents unauthorized access and maintains the privacy of the conversation.
By leveraging the Signal Protocol and its advanced cryptographic techniques, WhatsApp provides a secure platform for communication.
Whether you're sending messages, sharing multimedia, or making voice and video calls, end-to-end encryption ensures that your data remains private and protected.
Know How to Get Started with WhatsApp Marketing in Just 5mins!
Limitations and Considerations of End-to-End Encryption
While WhatsApp’s end-to-end encryption provides robust security, there are still potential vulnerabilities and limitations that users should be aware of. This section discusses these challenges, offers ways to mitigate risks, and provides guidance on managing and securing WhatsApp backups.
Potential Vulnerabilities and Limitations of WhatsApp’s Encryption
Key Management Issues
- Key Loss: If users lose their device or forget their encryption key or PIN, they may permanently lose access to their encrypted messages.
- Key Distribution: Securely exchanging encryption keys between users can be challenging. If the keys are not handled properly, they could be intercepted.
Metadata Exposure
While message content is encrypted, metadata such as who you communicate with, when, and for how long is not encrypted. This data can still provide valuable insights to third parties or attackers.
Backups and Cloud Storage
If not properly encrypted, backups stored on cloud services like Google Drive or iCloud can be vulnerable to unauthorized access. By default, these backups are not end-to-end encrypted.
User Errors
Users may unintentionally compromise their security by falling victim to phishing attacks, using weak passwords, or failing to verify the identities of their contacts.
Compatibility Issues
E2EE requires both parties to use compatible software. If one party is using a non-encrypted platform, the communication will not be secure.
Device Security
If an attacker gains physical access to a user’s device, they could potentially access the decrypted messages directly from the device.
Government and Regulatory Challenges
Some governments have expressed concerns over E2EE because it limits their ability to access communications for law enforcement purposes. This has led to legal and regulatory challenges for platforms like WhatsApp.
Addressing Real-World Challenges and How Users Can Mitigate Risks
Enable Two-Step Verification
Users should enable two-step verification to add an extra layer of security. This feature requires a PIN when registering your phone number with WhatsApp, preventing unauthorized access.
Use Strong, Unique Passwords
Users should use strong, unique passwords for their devices and cloud storage accounts to prevent unauthorized access.
Regularly Update the App
Keeping WhatsApp updated ensures that users benefit from the latest security features and patches for known vulnerabilities.
Verify Contacts
Users should verify the identity of their contacts by checking security codes. This ensures that the communication is secure and not intercepted by a third party.
Be Wary of Phishing Attacks
Users should be cautious about unsolicited messages or links, especially those asking for personal information or login credentials.
Secure Device Access
Users should protect their devices with strong passcodes, biometric locks, and remote wipe capabilities to prevent unauthorized access if the device is lost or stolen.
Limit Metadata Exposure
While users cannot fully eliminate metadata exposure, they can minimize it by limiting unnecessary communication and being mindful of the information shared.
By understanding the challenges and limitations of WhatsApp’s encryption and taking proactive measures to secure their communication and backups, users can significantly enhance their data privacy and security on the platform.
20 Battle-Tested Strategies to Boost Your Sales on WhatsApp
Best Practices for Securing WhatsApp Backups
Managing and securing WhatsApp backups is crucial for preserving chat history while maintaining privacy and security. Here are some best practices:
Enable Encrypted Backups
WhatsApp offers end-to-end encrypted backups. Users should enable this feature to ensure that their chat history is encrypted and only accessible to them.
- For Android: Go to WhatsApp > Settings > Chats > Chat backup > End-to-end encrypted backup.
- For iOS: WhatsApp backups to iCloud are encrypted by default.
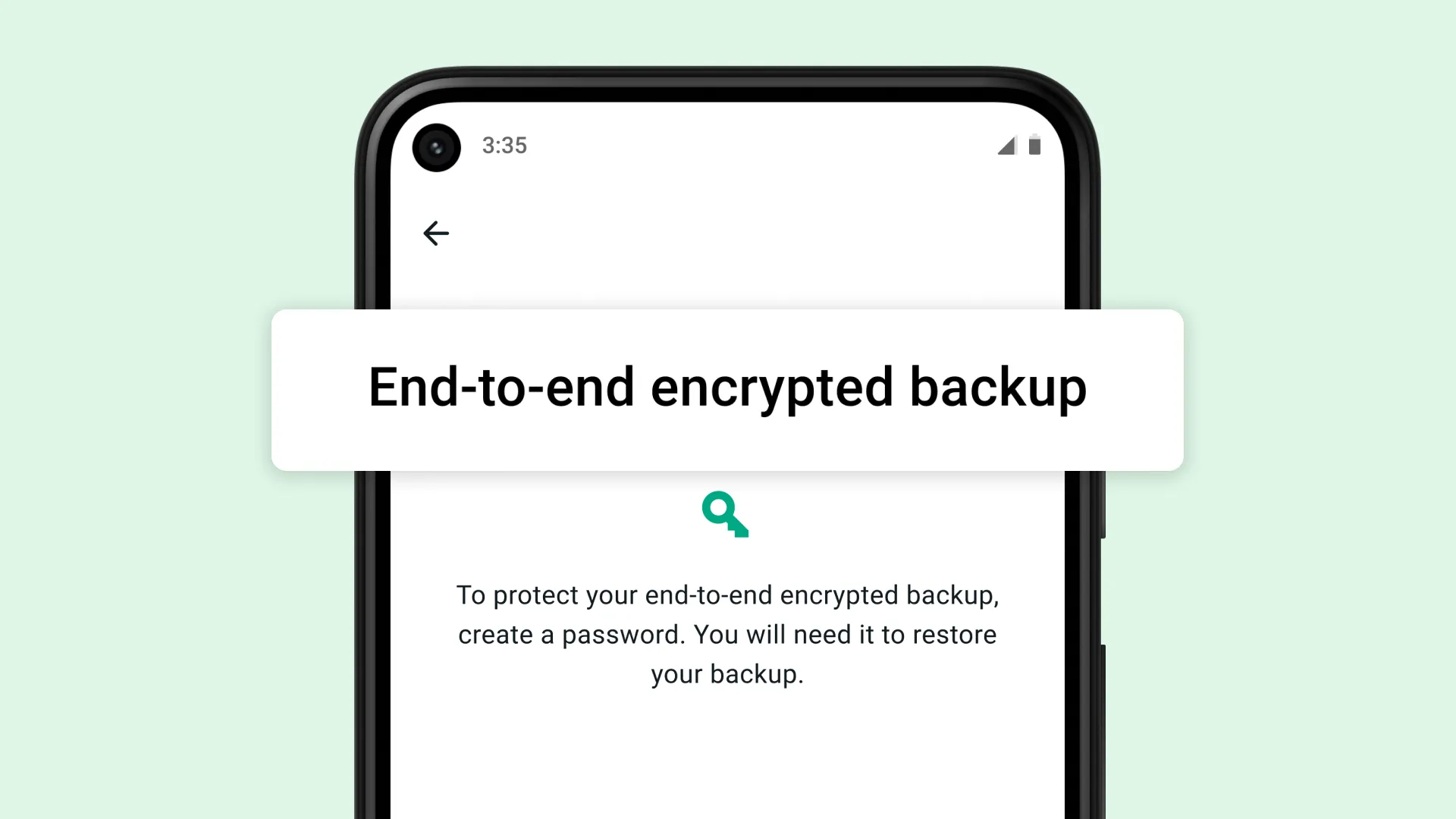
Use Strong Backup Passwords
When setting up encrypted backups, users should choose strong, unique passwords. This password will be required to restore the backup.
Secure Cloud Storage Accounts
Users should enable two-factor authentication for their cloud storage accounts (Google Drive or iCloud) to add an extra layer of security.
Regularly Check Backup Settings
Users should regularly review their backup settings to ensure they match their preferences. This includes backup frequency and the inclusion of videos in backups.
Manage Backup Storage
Users should monitor their cloud storage space and delete old or unnecessary backups to free up space and reduce potential security risks.
Be Cautious with Third-Party Backup Services
Users should avoid using third-party apps or services for WhatsApp backups. Stick to the official backup options provided by WhatsApp to ensure security.
Common Myths and Misconceptions About WhatsApp Data Security
Despite WhatsApp's strong security measures, several myths and misconceptions about its encryption and data privacy persist. This section aims to address these common myths and clarify some prevalent concerns, particularly regarding Facebook's access to WhatsApp data.
Myth 1: WhatsApp Reads Your Messages
Clarification:
- End-to-End Encryption: WhatsApp uses end-to-end encryption, ensuring that only the sender and recipient can read the messages. WhatsApp itself cannot read or access the content of your messages, calls, photos, videos, and other media.
- Encryption Keys: The encryption keys used to encrypt and decrypt messages are stored on the users' devices, not on WhatsApp’s servers. This means that even if WhatsApp wanted to, it couldn't read your messages.
Myth 2: WhatsApp Shares All Your Data with Facebook
Clarification:
- Data Sharing for Specific Purposes: While WhatsApp does share certain data with Facebook, this primarily includes metadata such as phone numbers and device information. This data helps improve services like spam prevention and targeted advertising on Facebook.
- No Access to Message Content: The content of your personal messages, calls, and media remains end-to-end encrypted and is not shared with Facebook. Personal communication stays private and inaccessible to any third party, including Facebook.
Myth 3: WhatsApp Stores All Your Chats in the Cloud
Clarification:
- Optional Cloud Backups: WhatsApp offers the option to back up chats to cloud services like Google Drive (for Android) or iCloud (for iOS). These backups can be encrypted to ensure that only you can access them.
- Encrypted Backups: In 2021, WhatsApp introduced the option for end-to-end encrypted backups, adding an extra layer of security to cloud-stored chat histories.
Myth 4: WhatsApp Listens to Your Calls
Clarification:
- Encrypted Calls: Voice and video calls on WhatsApp are secured with end-to-end encryption. This ensures that calls are private and cannot be intercepted or listened to by WhatsApp or any third party.
Myth 5: WhatsApp Has Access to Your Contacts’ Data
Clarification:
- Limited Data Collection: WhatsApp periodically accesses your contact list to identify other WhatsApp users and facilitate communication. However, this data is not stored on WhatsApp’s servers or shared with third parties for marketing purposes.
- User Control: Users have control over who can see their profile information and who can contact them, ensuring privacy and security.
Myth 6: WhatsApp Tracks Your Location at All Times
Clarification:
- User Consent Required: WhatsApp allows users to share their real-time location with contacts, but this feature is optional and requires explicit user consent.
- Temporary Sharing: Location sharing is time-limited and can be turned off at any time by the user. WhatsApp does not continuously track your location.
Myth 7: WhatsApp Reads Your Messages for Spam or Ads
Clarification:
- Metadata Analysis: WhatsApp uses metadata (such as message timestamps and contact information) to detect and prevent spam. However, the actual content of messages remains encrypted and inaccessible.
- Ad-Free Messaging: WhatsApp does not use message content for advertising purposes. Any ads seen on Facebook or Instagram are based on data from those platforms, not WhatsApp messages.
Myth 8: WhatsApp Does Not Prioritize Privacy
Clarification:
- Privacy as a Core Principle: Privacy and security are fundamental to WhatsApp’s service. The platform implements end-to-end encryption by default and continuously updates its security features to protect user data.
- User Empowerment: WhatsApp provides users with robust privacy settings, including two-step verification, encrypted backups, and control over who can see their profile information.
Myth 9: WhatsApp Data is Not Secure
Clarification:
- Robust Encryption: WhatsApp’s use of the Signal Protocol for end-to-end encryption ensures that user data is secure. Regular security audits and collaborations with security experts help maintain high-security standards.
- Constant Updates: WhatsApp continuously enhances its security features to address new threats and vulnerabilities, ensuring that user data remains protected.
Myth 10: WhatsApp Keeps Track of Your Payments Data
Even though WhatsApp lets you send and receive money, it doesn't hold onto your payment information. They follow high-security guidelines to keep your financial data safe.
By addressing these common myths and misconceptions, users can better understand the robust security measures WhatsApp has in place and feel more confident in the platform’s commitment to privacy and data protection.
Introducing DoubleTick
DoubleTick is designed to empower your sales team to sell more in less time. It's one of the best WhatsApp Marketing tools that comes with premium WhatsApp API features such as a cloud-based shared team inbox, unlimited WhatsApp broadcast messaging, dynamic catalogue sharing, advanced Chatbot, order booking bots, and much more.
Sign up with DoubleTick today and transform WhatsApp into the ultimate sales engine to delight customers and drive revenue.
How to Get DoubleTick
Kindly email us at [email protected] or Click the Below Banner to get a FREE DEMO to learn about our product offering, features and pricing plans.
Now transform WhatsApp into the ultimate sales engine to delight customers and drive revenue with DoubleTick!
Or Download the application from the Playstore or Appstore
How to Get DoubleTick for FREE?
Step 1: Download the DoubleTick App
Navigate to the Play Store or Apple Store and download DoubleTick. You can also download the app here:
iPhone Users: Download Here
Android Users: Download Here
Step 2: Sign Up for a Free Demo Account
Before you commit, we want you to experience the power of DoubleTick firsthand. Sign up with DoubleTick and access the platform, where you can explore and test the features of the product.
From the Editor's Desk:
- 10 Best AiSensy Alternatives & Competitors in 2024 (Affordable & Best)
- How To Get a Verified Green Tick Badge on WhatsApp - A Step-by-Step Guide
- How to Schedule WhatsApp Messages - Ultimate Guide
- WhatsApp Marketing Made Easy- Learn How to Send Bulk Messages on WhatsApp
- What is WhatsApp Business API (Exclusive Guide) | 2024 Edition
- 50+ Best WhatsApp Promotional Message Templates That Work Like a Charm
- 10 Best WATI Alternatives & Competitors in 2024 (Affordable & Best)
Frequently Asked Questions
Question: Are video calls on WhatsApp safe?
Answer: Yes, WhatsApp video calls are protected by end-to-end encryption. This ensures that only you and the person you're communicating with can view or hear the content of the call.
Question: Are WhatsApp messages encrypted?
Answer: Yes, all WhatsApp messages are secured with end-to-end encryption. This means only you and the recipient can read the messages, and no one in between, not even WhatsApp, has access to them.
Question: How to encrypt WhatsApp chat?
Answer: You don’t need to manually encrypt WhatsApp chats—they are automatically encrypted using end-to-end encryption.
Question: Should end-to-end encryption be on or off on WhatsApp?
Answer: End-to-end encryption should always be on for your chats and calls to keep your conversations private and secure. It’s a default feature and cannot be disabled for regular chats and calls, but it can be turned off for backups.
Question: What is end-to-end encryption (E2EE) and how does it work on WhatsApp?
Answer: End-to-end encryption (E2EE) ensures that only you and the recipient can read the messages you send. Messages are encrypted on your device and decrypted only on the recipient’s device, preventing unauthorized access.
Question: Can WhatsApp read my messages or listen to my calls?
Answer: No, WhatsApp cannot read your messages or listen to your calls. With E2EE, messages and calls are encrypted from sender to recipient, ensuring privacy and security.
Question: What data does WhatsApp share with Facebook?
Answer: WhatsApp shares limited data with Facebook, such as phone numbers and device information, to improve services like spam prevention. However, the content of messages and calls remains private and encrypted.
Question: How can I ensure my WhatsApp backups are secure?
Answer: You can enable end-to-end encrypted backups in WhatsApp. This ensures that your chat history is encrypted and can only be accessed by you. Go to Settings > Chats > Chat backup to enable this feature.
Question: What should I do to protect my WhatsApp account from unauthorized access?
Answer: Enable two-step verification in WhatsApp, use a strong password for your device and cloud storage accounts, and be cautious of phishing attempts. Regularly update the WhatsApp app to benefit from the latest security features.
Question: What’s DoubleTick’s pricing plan?
Answer: Kindly email us at [email protected] or Click here to BOOK a FREE DEMO with us to learn about DoubleTick’s features and pricing plans.
Question: How many team members can I add to my DoubleTick account?
Answer: You can add unlimited team members to DoubleTick.
Question: In how many days will the DoubleTick setup be ready for my WhatsApp Business account?
Answer: If your Meta Business Manager is verified, you can get started with DoubleTick within 5 minutes. If however, you need help with Meta Business Manager verification then the process will take around 3 days to a week depending on how ready you are with your documents as well as the response time from Meta.
Question: Can I use my existing number for DoubleTick?
Answer: Yes, you can use your existing number with DoubleTick. However, we would recommend that you use a new number instead of using an existing one to ensure smooth operations for your business.
Question: Can I use my WhatsApp business app number and DoubleTick number at the same time?
Answer: No, at a time you can use only one account. Data from your WhatsApp business account will be erased once you switch to DoubleTick.
Question: To how many customers can I shoot the broadcast messages?
Answer: There is no restriction. You can create unlimited broadcast groups and shoot messages to unlimited contacts. However, Meta might restrict you if a lot of customers mark your message as spam. The best practice is to enable the STOP bot on DoubleTick and send your templates with a STOP quick reply message so that people who are not interested in your communication can easily press STOP to opt out instead of reporting your number as SPAM to WhatsApp.
Question: Can I automate and schedule broadcast messages?
Answer: You can automate WhatsApp messages and schedule broadcasts with DoubleTick.
Question: Does DoubleTick come with a bulk contact upload feature?
Answer: Yes, you can simply upload an Excel file having contact details to the dashboard and shoot messages in bulk to unlimited customers.
Question: How many devices does DoubleTick support?
Answer: An unlimited number of devices can be used with DoubleTick. However, access to the number of accounts will be based on your subscription.
Question: Can I integrate WhatsApp Business API with my existing CRM system?
Answer: Yes, many WhatsApp Business API providers, such as DoubleTick offer seamless integration with popular CRM systems, ERP, and other tools.
Question: Do WhatsApp Business API providers offer automation features?
Answer: Some providers offer built-in automation features and AI-powered chatbots, while others may require custom development or third-party integrations for advanced automation. With DoubleTick you get advanced WhatsApp automation features that can be tailored to your needs. DoubleTick's no-code WhatsApp chatbot panel enables you to perform unlimited automation as per your business requirements.
Question: Is WhatsApp Business API secure?
Answer: Yes, WhatsApp Business API uses end-to-end encryption to ensure the security and privacy of your customer communication.
Question: How much does it cost to use WhatsApp Business API?
Answer: Pricing varies depending on the provider and your usage levels. Some providers offer pay-as-you-go pricing, while others may have tiered pricing plans.
Click here to check out our pricing plans or book a FREE demo with us to know more about the product and its features.